

As technology advances with lightning speed, it improves the quality of life and the things that we can do on the internet. But at the same time, like all other times in human memory, technology is much like a coin with two faces. A productive face and a destructive one. Online attacks and malicious hacking is one destructive aspect of the web that has seen a massive surge in utilization in the past decade. The methodology is also getting more sophisticated. One of the most commonly used online attacks is the distributed denial of service attack, known in short as DDoS. DDoS itself is an evolved and more advanced form of the DoS (denial of service) attack. Whereas many different online attack methods, such as the notorious Trojan virus were once feared and now have become obsolete, the DDoS way of attacking a network or server has stood the test of time and continues to be used to this day with great success. Of course, there are methods to combat it and prevention methods to take into account. But what can we do when our home network is under attack? In this article, I will go over ten solutions and prevention methods for DDoS protection for home networks. But before we jump ahead of ourselves, let’s get our definitions right.
What Is a DDoS Attack?
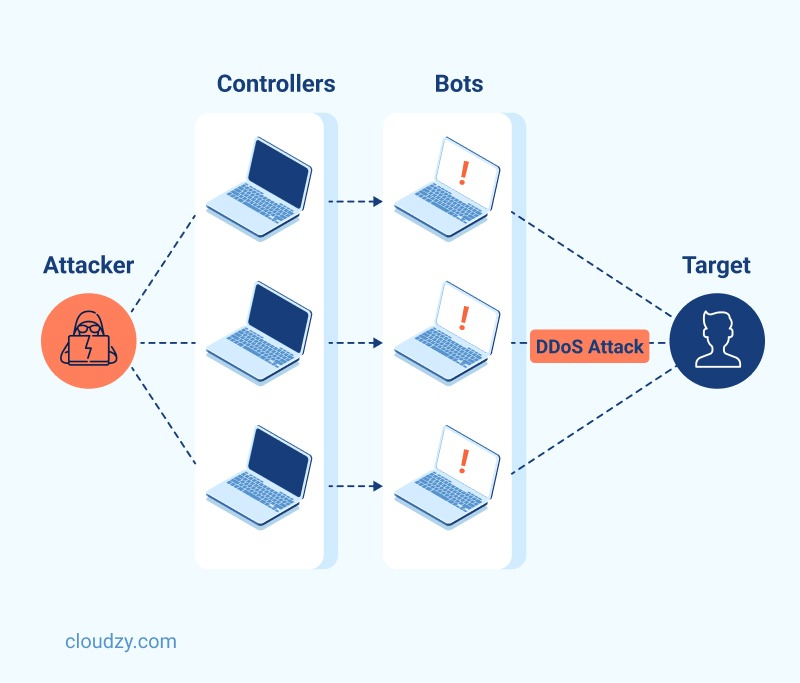
Unlike the popular imagination, DDoS is an attack and not a hacking operation. This means that the attacker who is behind the DDoS attack is not seeking to wrest control of your network or server. Rather, they want to take it out of operation and crash it. While there are several different DDoS attack methods that fit into three general categories, the overall scheme for all of them more or less follows the same pattern. In a DDoS attack, the attacker overloads the network or server in question with a massive wave of illegitimate networking requests.
The sheer velocity and volume of these fake requests are so high that it takes over the bandwidth of your network or server and forces it to devote all its resources to process these requests. Therefore the server will either not respond to other tasks and requests due to a lack of processing resources, or otherwise crash and burn completely. The attacker usually launches these attacks via a number of devices that have been scripted to spam requests; these devices are employed as part of a “botnet” network. Since home networks run on allocated bandwidth from a central server belonging to your ISP, taking them out with DDoS is rather easier compared to a server you run yourself. This necessitates router DDoS protection.
[rh-cta-related pid=”12058″]The Three Types of DDoS Attacks
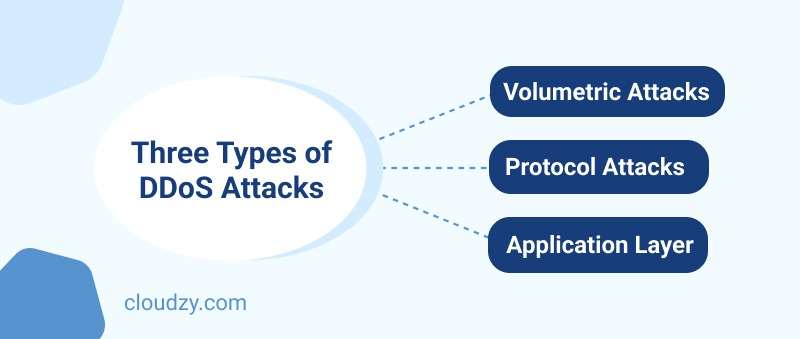
It is important for you to know the three general categories that a DDoS attacker will employ to cause damage to your home network. These three categories are not attacking methods themselves, but rather they are attacking schemes that each have several different DDoS attacking methods within themselves. Let’s quickly evaluate them.
Volumetric Attacks
As the name suggests, attacks following the volumetric category rely on sheer volume to successfully make an attack happen. Because of this, they are also the most commonly used type of DDoS attack to happen. The process is rather straightforward. The attacker will simply rely on the quantity and send as much illegitimate traffic as possible in order to crash the server. The hacker will target your DNS. If the first wave of requests and unwanted traffic was not enough, they could simply send it again and again. Volumetric attacks are common because they are easy to perform by almost anyone. Luckily this also means that the process of DDoS protection for home networks is easier against this method.
Protocol Attacks
Protocol-based attacks require a little bit more effort to perform, but in exchange, their effects are also much more devastating on a home network. The attacker in this method needs a basic level of communication to be established between your network and theirs. Therefore they will send what is known as a “TCP” handshake. Accepting this handshake will exchange a set of initial data, including IP and DNS addresses. The hacker then will not complete the handshake request. Instead, they use the newly acquired data to keep making TCP handshake requests with fake IP addresses after fake IP addresses. These requests need bandwidth to process and even reject. Therefore the server will be overloaded and shatter.
Application Layer
Application Layer DDoS attacks are the most clever method of attack since they will use an application or a server’s own hosted resources against itself. The name also implies that rather than going after the basic infrastructure of the server, the attack instead takes place on the “application layer” of whatever data is hosted on a server. If that is a website, the hacker will continually request an illegitimate subsection of that website to be loaded. When this happens the webpage has to inform them that no such subsection exists with a response package. The attacker will keep requesting the page until the server is overwhelmed and can no longer respond to their or anybody else’s requests, be legitimate or illegitimate.
[rh-cta-related pid=”19616″]The Zero Day and Other DDoS Attack Methodologies
Now, each of the three aforementioned categories of DDoS attack also has a number of attacking methods that fall under their umbrella. The most common attacking methods in the protocol attacking category are TCP flood and SYN flood. With volumetric attacks, we have the ICMP flood, ping of death, and UDP flood. Finally, with the application layer, we have the slowloris method. All of these methods are well documented and there are ways to counteract them both on home networks and independent servers. But there is also another category of DDoS attacks known as Zero Day attacks. As the name implies, these attacks are methods that are yet to be discovered and their existence only comes to light when they are first used against a new victim. The fluidity of the concept concerning DDoS attacks means that there are many different zero-day attacks using new and innovative attacking methods. Zero-day attacks are considered precious because their protocol is yet to be discovered. Therefore it is hypothesized that these methods are being saved from being used against major targets. All the different methods I named earlier were also once called zero-day attacks. Generally, however, these attacks are the last thing you need to worry about concerning DDoS protection for your home network.
HTTP flood is also a prominent DDoS attack. In order to protect yourself from being exposed to it, it is highly advised that you protect your HTTP while browsing online on browsers such as Chrome.
[rh-cta-related pid=”19393″]Motivations Behind a DDoS Attack
There are different motivations behind each DDoS attack. But in general, there is a pattern to be followed concerning the root causes of these attacks. The larger DDoS attacks usually happen for two reasons. First is extortion. When a group of hackers successfully disables a business’s online reach, they are severely hampering its marketing and operational capacity. Therefore the victim often finds it easier to simply pay the attackers to lift the DDoS attack. Another reason behind large-scale DDoS attacks is to send a political message or take part in social activism.
However, when a DDoS attack is taking place against a home network, the reasons can be a little different. When a home network specifically is targeted with DDoS, the reasons usually are personal. If not, then you or your ISP have most likely fallen victim to an extortion scheme. It is known that some gamers also use DDoS against other gamers in multiplayer sessions in order to create lag for opponents and gain an advantage for themselves. Overall, the chances of being attacked personally on your home network with a DDoS attack are low, but what to do when it actually happens? Here are ten solutions to protect your home network from DDoS.
10 Methods for DDoS Protection on Home Network
Before we get to explaining each of these methods, it is important to note that none of these solutions are absolute in defending against a DDoS attack against your home network; instead, they must be used in conjunction with one another in order to prevent DDoS on the home network.
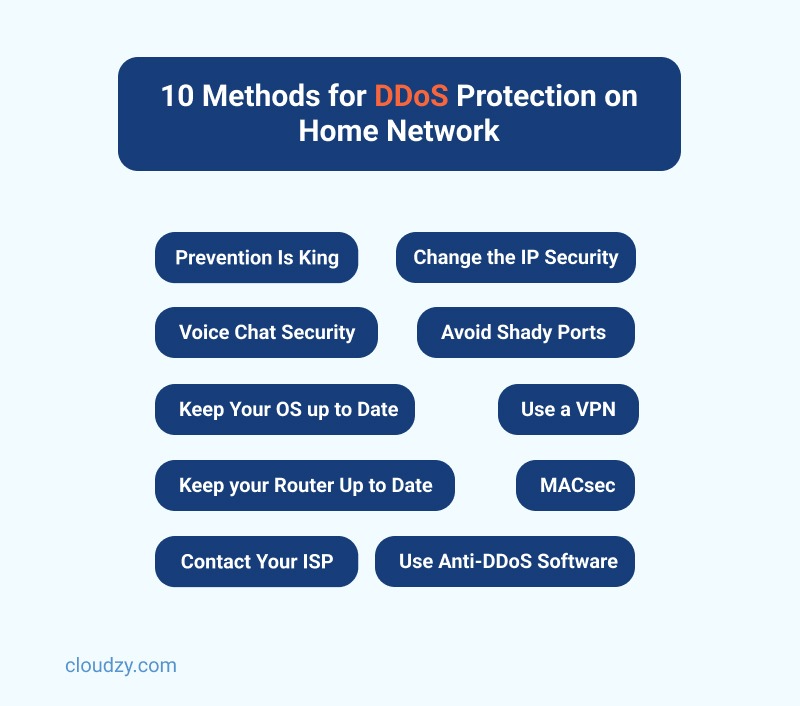
1. Prevention Is King
This one is not actually a technical method to fight DDoS attacks; instead, it is more of a mindset. DDoS attacks are the most common type of online malicious activity. Therefore, as unlikely as it may be for your home network to suffer a DDoS attack, it is still highly advised for you to conclude your own research and have all the punitive, cautionary, and preliminary actions that you can muster in place. No victim of a successful DDoS was ever prepared for it. This clearly showcases that some of the options that we are about to explore further down the article need to be implemented now. Before the attack actually comes on your home network.
2. Change the IP Security
Your IP address is your online identity, and it is the primary means of recognizing you and your devices and network in the online world. Therefore it is also the primary avenue from which attacks will constantly be launched against you in a hypothetical attacking scenario. It is advised that while you partake in risky online activity, mask your IP address. Better yet, you can use an evolving IP address strategy by having your ISP change your allocated IP address from time to time. This will make targeting you much much harder.
[rh-cta-related pid=”24768″]3. Use a VPN
A lot of DDoS attackers usually target a large list of IP addresses that they gather from public domains. There is always a chance that your IP address is also found in one of these domains. Therefore, in line with the IP security matter that I mentioned above, a good solution is to use a virtual private network. This VPN will not only completely mask and alter your actual IP address, but it will also encrypt your data. This will make launching a successful DDoS attack against your home network considerably harder to perform. So this is another reason why to use a VPN.
4. MACsec
IEEE 802.1AE, also known as MACsec, is a networking protocol that will essentially make certain aspects of your connection, such as Ethernet and VLAN, bulletproof against any overwhelming DDoS force. Now, configuring a MACsec protocol in order to provide DDoS protection for a home network is a rather difficult and complicated method. Despite this, it remains one of the most effective methods in preventing attacks such as man in the middle and DDoS. If your home network constantly suffers from DDoS, getting MACsec implemented will go a long way in protecting you.
5. Use Anti-DDoS Software
This is by far the most straightforward it can get. An anti-DDoS software is designed specifically to recognize the patterns that are used by the different methods of DDoS attacks. After successfully determining the incoming traffic to be malicious, it will simply block communication or otherwise completely sever the link between the malicious device and your network by blocking their IP. There are a lot of credible options as far as anti-DDoS programs go, like SolarWinds’ Security Event Manager, which will also protect you against attacks used to exploit remote access protocols such as SSH.
6. Keep Your OS up to Date
I cannot stress enough how important it is for you to have your operating system up to date. And that extends to all the devices that are connected to your home network. Whether it is Linux, macOS, or Windows on your desktops, or if you have Android or iOS on your phones, it is imperative that you have them all updated to the latest version. Outdated OS versions are one of the most exploited weak points in security that facilitate all manners of attacks against you by allowing the hacker to first infiltrate the outdated device before launching an attack on the network.
7. Avoid Shady Ports
A lot of us use different entertainment and communication software every day that uses certain transmission ports in order to transfer data between our device and their services. The prime examples are Steam, Netflix, Discord, Skype, Spotify, Xbox Live, etc. While there are official ports that are secure, there are also alternative ports that can be used to solve some bugs or access new content. However, it simply is not worth your network security and I advise you to under no circumstance use these shady ports and always stay with the officially stated ports for each service. Otherwise, establishing linkup for attacks such as TCP flood becomes really easy for an attacker.
8. Keep your Router Up to Date
This is another crucial aspect of your home network security in general. Not only will this prevent DDoS on the home network, but it is also really helpful against all manners of online malicious activity directed at you. Similar to the devices connected to the network, modems, and routers also issue software updates that are aimed at improving security. Older versions subsequently have weakened security compared to later versions. Getting your router infiltrated is the worst-case scenario, as it will act as both the central target of the attack, but also the attacker since the malicious party will use the router itself to overload the network. Keep the routers up to date!
9. Voice Chat Security
It is also known that services such as Skype and even the likes of Discord can have compromised base levels of security. This allows a malicious attacker to load up a simple audio chat or video call request with a UDP packet in order to establish a handshake and then proceed with an all-out DDoS attack. Therefore, as a general rule, never accept requests for audio chats or video calls from people that you don’t know on the web. This is in line with the first tip of the article to always have a defensive state of mind in order to prevent DDoS attacks rather than solve them when they occur. It’s also best to use communication software that does not expose you.
10. Contact Your ISP
If you simply do not have the computer knowledge to perform the different solutions on this list, or if an all-out attack has already happened against you to the extent that the network is entirely unresponsive, then your only solution is to contact your internet service provider. As the admins of the server, they can change your IP address to lift the ongoing attack and then block the responsible IP address that was launching the DDoS attack against you. A lot of ISP options also offer base-level DDoS protection, so choosing one of them also helps a lot!
Conclusion
DDoS attacks are by far the most painful type of online malicious activity that a person has to deal with. While the damages are not directed at your personal information, the difficulty in tracking the attacker and lifting the attack makes it extra annoying. DDoS attacks are not limited to a specific type of server and host. They can also happen when you are using remote access services such as a VPS. Therefore it is highly advised that you opt for a VPS provider that not only has high levels of base security with regards to DDoS attacks but can immediately lift the attack in case it actually happens. Cloudzy offers premier DDoS-protected VPS services that will put your mind at ease from DDoS concerns for good. Cloudzy also feature more than 15 locations, tailored packages, excellent connectivity, an uptime rate of 99.95%, and even a seven day money back guarantee!
[rh-cta-buy type=”2″ ]
FAQ
Can a Home Network Be DDoS Attacked?
Yes. Not only it is possible, but since home networks are allocated a certain amount of resources from a central server, they are especially vulnerable to crashing under the weight of a capable DDoS attack.
Are there Routers with DDoS Protection?
Yes. And it is highly advised that you use them. Since they come in software form, some of the older routers that did not originally have anti-DDoS add them with updates. Hence the importance of updating your router.
How to Detect a DDoS Attack on my Home Network?
There are several signs that a DDoS attack is ongoing against you. These include a severe reduction in network speed and time-out errors. Traffic spikes that follow a pattern are also a clear indicator.


