

If you’re a Linux network administrator, it’s highly important for you to know about ports and how to manage services on a network by manipulating them. Even normal Linux users may need to run these tasks. Imagine you want to access a port remotely. How would you do that if you don’t know whether it’s open? In this blog, we’ll talk about listing Linux ports and review all the possible ways you can check open ports in Linux.
[lwptoc]Network Ports 101
You may have heard about ports before. When it comes to networks and connections, the word port combined with a number is tossed around to explain how different parts of a network are exchanging data. But what exactly is a port?
Imagine a network of computers that are actively communicating with each other. These communications make up all the connections in the network. On each side of a single connection, there’s something called a socket. A socket has two parts: An IP address and a port number. A port is a designated space that is the destination of internet traffic. Each port can be used with different transport protocols like UDP, TCP, SCTP, and DCCP. The number that’s assigned to a port is not just a random number. It says a lot about the port’s use cases. The number can range between 0-65535.
- Ports ranging from 0 to 1023: called system or well-known ports.
- Ports ranging from 1024 to 49151: registered ports.
- And ports ranging from 49152 to 65535: dynamic ports.
For our means and purposes, we’ll be focusing on well-known ports since they have more general usage. Here’s a table of the most important well-known ports with complementary information about their transport protocols.
| Port Number | Transport Protocol | Service |
| Port 22 | UDP/TCP/SCTP | SSH |
| Port 25 | UDP/TCP | SMTP |
| Port 53 | UDP/TCP | DNS |
| Port 80 | UDP/TCP | WWW/ HTTP |
| Port 123 | UDP/TCP | Network Time Protocol |
| Port 443 | UDP/TCP | HTTPS |
Dynamic ports are also important in daily network communications. A client uses these ports to connect to a server. The server’s receiving port can be either well-known or registered. For example, when you search for a dog photo, your browser opens the connection using a dynamic port and reaches port 80 on the web server.
Processes transfer data using UDP or TCP protocol. Since it’s possible for a process to use both protocols, processes can deploy different port numbers for each protocol. Any given port can be used only by one process at any given time. So, when a port is occupied by a process, it can’t be used by another one until the first process ends.
All this information comes in handy when you want to change the port’s processes run on. In the next section, we’ll talk about why you may need to change a process’s port.
Why Do I Need to Manipulate Ports?
Now that you know the basics about ports, you may want to know what is the purpose of manipulating them. Is it just security? Manipulating ports serves several important purposes in network administration, as well as application development:
Network Security
Manipulating ports allows network administrators to implement security measures to protect their systems. They can close or restrict access to specific ports to stop unauthorized access or mitigate potential threats. Port manipulation gives administrators a chance to define firewall rules, configure access control lists, and set up port forwarding to enhance the overall security of their networks.
Application Development
Developers may need to manipulate ports when creating networked applications. For example, when they develop a client-server application, the server application listens on a specific port for incoming connections from client applications. Changing ports allows developers to establish communication channels, implement protocols, and ensure proper data exchange between client and server.
Methods to Check Open Ports in Linux
In this section, we will explore different methods to check open ports in Linux, providing you with a range of options depending on your preferences and requirements.
Using Command-Line Tools to Check Open Ports in Linux
The most common method to check open ports in Linux is utilizing command-line tools. Several tools are available for this purpose, including netstat, nmap, and ss. Let’s look closely at each one of them.
Using netstat for Checking Open Ports
This tool displays active network connections, listening ports, and various network statistics. To ask Linux list open ports, you can use the -l option to list listening ports or the -a option to display all sockets, including established connections. The output will provide information about the port number, protocol, local address, foreign address, and connection state. So, netstat is a great command to check used ports Linux. But before using it, you need to install the netstat package. Use the following line to install netstat package:
apt install netstat
Use netstat -l command to check Linux port usage:
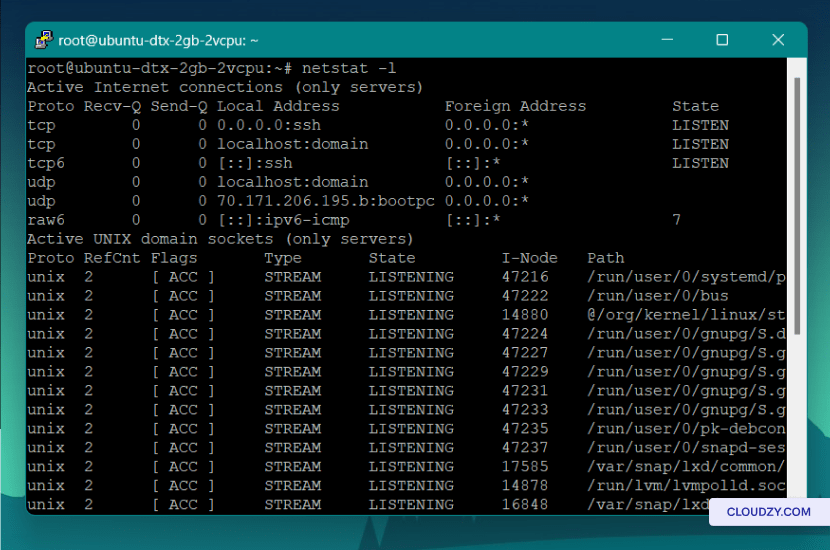
In the first section of this screenshot, you can see six columns. Here’s what each column tells us:
- Proto: This column shows the protocol that’s being used for the connection, such as TCP (for TCP/IP) or UDP (for UDP/IP).
- Recv-Q: The receive queue size, which represents the amount of data waiting to be received by the local application from the network.
- Send-Q: The send queue size, which represents the amount of data waiting to be sent from the local application to the network.
- Local Address: This column shows the IP address and port number on the local machine to which the connection is bound. In our example, it includes both IPv4 and IPv6 addresses.
- Foreign Address: The IP address and port number of the remote machine or endpoint with which our machine is making an active connection.
- State: The state of the connection, indicating its current status. Two important states are “LISTEN” and “ESTABLISHED.” The first one indicates that the port is actively listening for incoming connections. The second one indicates that an active connection is established.
Analyzing the output of netstat and understanding the meaning of each column gives you more insights into the current network connections and the state of open ports on your Linux system.
Using nmap to Check Open Ports in Linux
Nmap is a powerful and feature-rich port scanning tool. It allows you to scan a range of IP addresses or specific hosts for open ports. By specifying the target IP or host and the desired scan options, such as -p to specify ports or -F for a faster scan, you can gather detailed information about open ports and the services running on them. You can use the following line of code to install nmap packages:
apt install nmap
And this line of code can be a great source to get a summary of nmap options:
nmap -h
You can simply use nmap with the IP address or the hostname of the system that you want to scan. Use this line of code do so:
nmap [IP address]
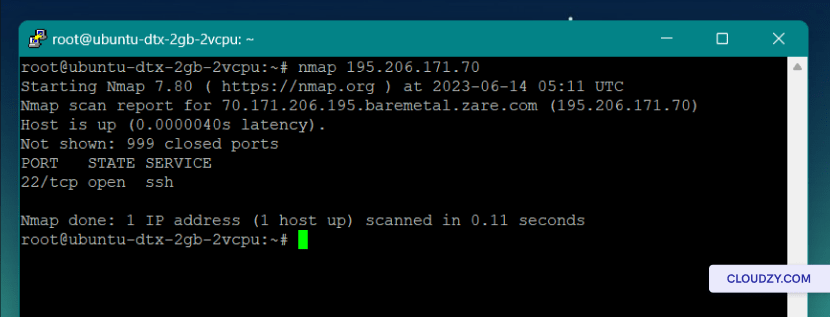
In this example, you can see that there’s only one open port on this system: port 22 for ssh connection.
You can also use nmap command to get information about a specific port and check if a port is open Linux. For example, this line of code scans ports 80 and 443:
nmap -p 80,443 [IP address]
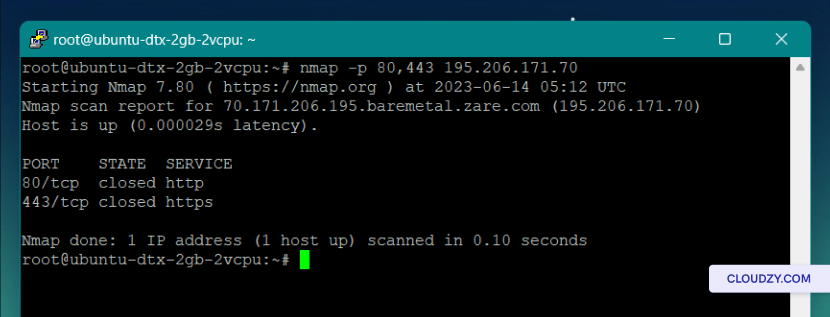
As you can see in the result of our scan, both of these ports are closed.
Using ss to Check Open Ports in Linux
The ss command is short for socket statistics. ss is pretty similar to netstat; only it provides more advanced filtering and display options. You can use it for Linux show open ports, listening sockets, and established connections. By using various flags, such as -l for listening sockets or -n to display port numbers instead of service names, you can obtain specific information about open ports.
For example, you can filter all the open ports and only see established TCP connections:
ss -t -a
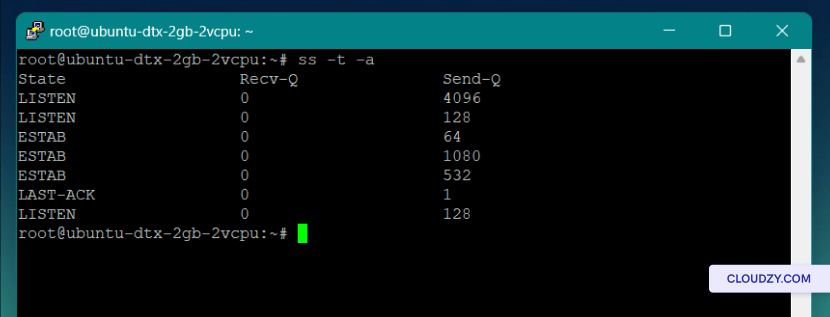
You can get the same information for all the established UDP connections using this command:
ss -u -p
And even if you want to see if there’s a TCP connection on a specific port, you can use the ss command. For instance, the code below checks for established TCP connections to port 80:
ss -t -a 'sport = :80'
Graphical Utilities
There are other options except the command line to check open ports in Linux. For example, if you use a desktop environment like GNOME, you can use applications that allow you to get a list of active processes and the ports that are associated with them by navigating to the “processes” or “networks” section. On GNOME, for example, there’s the GNOME System Monitor app that provides information about the processes of your Linux machine.
Besides using the command line, Linux users have alternative methods to check open ports, particularly when working within a desktop environment. For instance, within the GNOME desktop environment, one can utilize tools designed for monitoring system activities. A notable example is the GNOME System Monitor application. This tool offers insights into the processes running on your Linux system, including details about the ports these processes are using. This can be users go-to way to check open ports in Linux. Additionally, for a more graphical approach, applications like Zenmap are available. Zenmap is not only great for checking open ports in Linux but also offers a suite of network scanning utilities, making it a comprehensive tool for users who prefer graphical interfaces.
Although graphical utilities are easier to use and provide a more visual output, the command line tool is way more flexible and offers more options. So, depending on the type of network scan, the task you have, or your technical expertise, you can choose the tool that suits your needs. What matters here is that you regularly check open ports in Linux to make sure no security threats are behind your door.
[rh-cta-related pid=”24768″]Summary
In conclusion, the fact that you regularly check open ports in Linux is an important aspect of network administration and security. Understanding the status of open ports allows you to ensure the proper functioning of services, identify potential vulnerabilities, and maintain a secure network environment. In this blog post, we explored various methods to check open ports using command-line tools like netstat, nmap, and ss.
The netstat command provides a simple way to display active network connections and check listening ports Linux. nmap is a powerful port scanning tool that also allows you to scan remote systems for open ports. It has a wide range of options and scanning techniques, so you can perform in-depth analysis and identify services running on specific ports. The ss command offers advanced filtering and display capabilities and provides a detailed view of open ports and network connections.
These command-line tools provide valuable insights into active connections, listening ports, and the overall security of your system. By staying vigilant and employing these techniques, your network infrastructure will remain secure and well-functioning.
FAQ
Can I check to see if a specific port is open on my Linux system?
Yes, by using a command line or graphical tool, you can check open ports in Linux. Netstat, nmap, and ss are three useful tools to check for open ports in Linux.
Can I check open ports on remote systems using command-line tools?
Yes, you can check open ports on remote systems using command-line tools such as nmap. Simply specify the IP address or hostname of the remote system as the target in the command. For example, in this line of code nmap [IP address], you can add the IP address of the remote system you want to scan and check if port is open linux.
Why is it important to regularly check open ports in Linux?
Regularly checking open ports in Linux is essential for network security and system administration. Open ports can expose services and applications to potential vulnerabilities. When you regularly review open ports, you can identify any unnecessary or unauthorized open ports and take appropriate actions to secure your system. Monitoring open ports also helps in troubleshooting network connectivity issues.


